It’s Time For CAPTCHA to Die
Here’s the situation: You’re on a website and you’re reading the content and you decide to fill out their contact us form. You fill in your name, email address, phone number, and type in a brief message about what you need. Then, before you click the submit button, you’re presented with this:
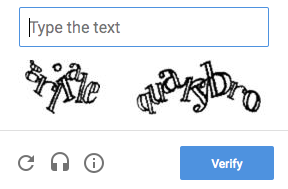
That’s a CAPTCHA. It is an acronym for “Completely Automated Public Turing test to tell Computers and Humans Apart.” Gosh, now that I look at the name, even that is convoluted.
Ok, so you begin to try to decipher the characters in the CAPTCHA above.
g
r
l? Is that an L or is it an i? Maybe the r and the l are actually (together) a larger n?
At this point, you’re probably incredibly frustrated and there’s a high likelihood that if you can’t figure out the CAPTCHA on the first or second try that you’ll abandon the form altogether… and maybe even the entire site.
So, why do websites use this complicated contraption? CAPTCHAs were invented back in the late 1990s by developers at AltaVista to keep automated website scripts (“bots”) from filling out website forms. The idea behind a CAPTCHA was that only a human would be able to decipher the characters and that a bot would always fail.
But then the bots become more intelligent (sounds like the Terminator movie franchise, right?) and could “read” the characters in the CAPTCHAs. So the developers started to make CAPTCHAs more visually complicated and the “arms race” began.
The point here is that CAPTCHA needs to die. It may have been a good idea years ago, but the truth is that CAPTCHAs are difficult for website visitors to use — and with the advances that hackers have made, CAPTCHAs aren’t even 100% reliable at preventing spammy form submissions.
What About Alternatives?
If we can’t keep the spam bots at bay with a CAPTCHA, how else can we protect our website from being spammed into oblivion? There’s actually quite a few interesting tactics that we can employ:
- Akismet: One of the top tactics that we currently use is a service called Akismet that will scan your form’s submission for known spam content such as known email addresses and keywords (viagra, cialis, etc.). Akismet claims that it blocks 7.5 million spam form submissions every hour on average and I believe it. It works very well in most cases. It is also included as a default plugin with WordPress since version 2.0.
- Question and answer challenge: What this means is that the form will present the website visitor with a question that requires knowledge that only a human would know. For example, you could ask what color the sky is. Or, you could ask a more site-specific question such as: What is the primary color of the Torx logo at the top of this website? We’ve also been known to use random math questions, such as: What does 2 * 4 =? Even though a human can easily answer any of those questions, an automated program that is scanning your website cannot.
- Honey Pot: This popular tactic involves creating an invisible form field that a human will never see (and therefore will never populate). On the other hand, automated bots usually populate all known fields of a form, even invisible ones. So when the form is submitted, if the honey pot field is populated, we know that the submission is spammy.
The above alternatives to CAPTCHA provide websites with sophisticated spam-blocking tactics, while keeping the user interface simple and user friendly, which leads to a higher percentage of website form completions.
If your website currently uses a CAPTCHA and you’d like to make it more user friendly, contact us and we can make your site more secure and easy to use.
About the author:
Jeff Pollard
Partner, Director of Technology
Jeff is one of Torx's founding partners and serves as the agency's Director of Technology. He built his first website back in 1996 and has never looked back. Jeff wears many hats at Torx: front-end designer and developer, server administrator, and resident Apple enthusiast.